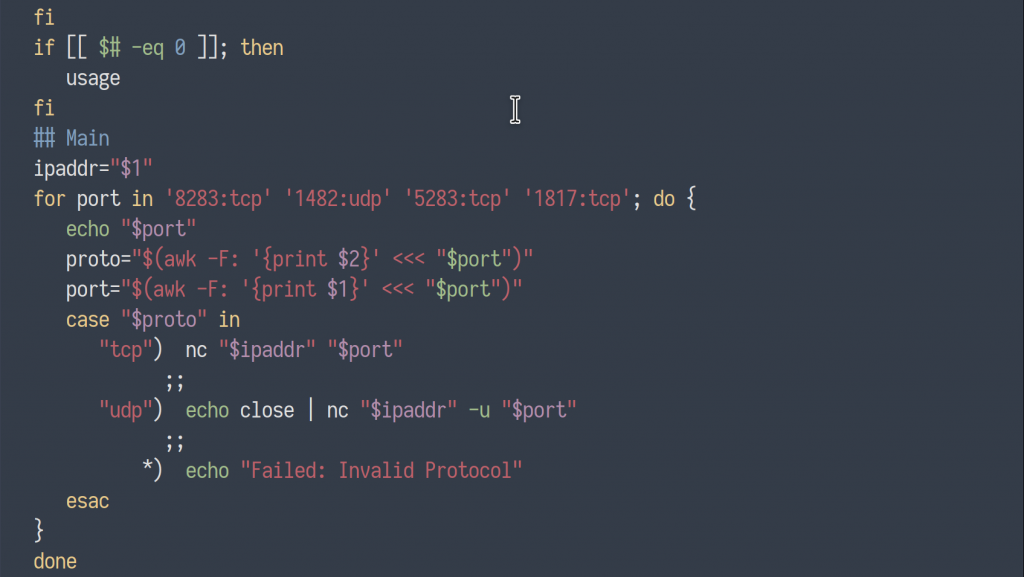
What is port knocking? Port knocking is a method of securing external facing services – explicitly blocked by firewall rules – by enabling firewall access only in the event that a correct sequence of connection attempts to random predetermined ports is attempted. Upon receipt of a correct sequence of connection attempts, the firewall rules are modified on the requested server, temporarily enabling access to the service for the requesting client.
The popular port knocking tool, Knockd, allows users to customize a variety of options to tweak their Knockd deployment. A user might customize the length of the port knocking sequence, the ports specified, the protocol (TCP/UDP), the packet’s flag type(s) (syn, ack, fin…), timeout period, and even an alternate sequence of ports to close the connection.
Before we jump into defining the steps needed to install a Knockd instance, let’s see it in action…
Preliminary Nmap Scan
To start, I have a CentOS machine on my local network (IP – 192.168.1.14) with an SSH server configured and enabled on port 22. Knockd has been enabled and a firewall rule has been configured to block all incoming traffic destined for port 22 (ssh).
Continue reading “Port Knocking & Knockd Configuration”