OverTheWire Leviathan – Level 1

Listing the directory of user leviathan1 reveals a ELF 32-bit executable with it’s SETUID bit set.
leviathan1@leviathan:~$ ls -la total 28 drwxr-xr-x 2 root root 4096 Oct 29 2018 . drwxr-xr-x 10 root root 4096 Oct 29 2018 .. -rw-r--r-- 1 root root 220 May 15 2017 .bash_logout -rw-r--r-- 1 root root 3526 May 15 2017 .bashrc -r-sr-x--- 1 leviathan2 leviathan1 7452 Oct 29 2018 check -rw-r--r-- 1 root root 675 May 15 2017 .profile leviathan1@leviathan:~$ file check check: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=c735f6f3a3a94adcad8407cc0fda40496fd765dd, not stripped
Execution of the check file prompts the user for password. By performing a simple strings ./check against the executable, a list of shared libraries, as well as, strings, including possible password love, are produced.
However, by executing check with the password love, we are met with an invalid password error.
Going forward, we can use the ltrace command, used to intercept and record dynamic library calls by the executable. Executing the command echo test | ltrace ./check, we are returned with an incorrect password, however, a strcmp() call can be observed, comparing the attempted password to the true password, not love, but sex.
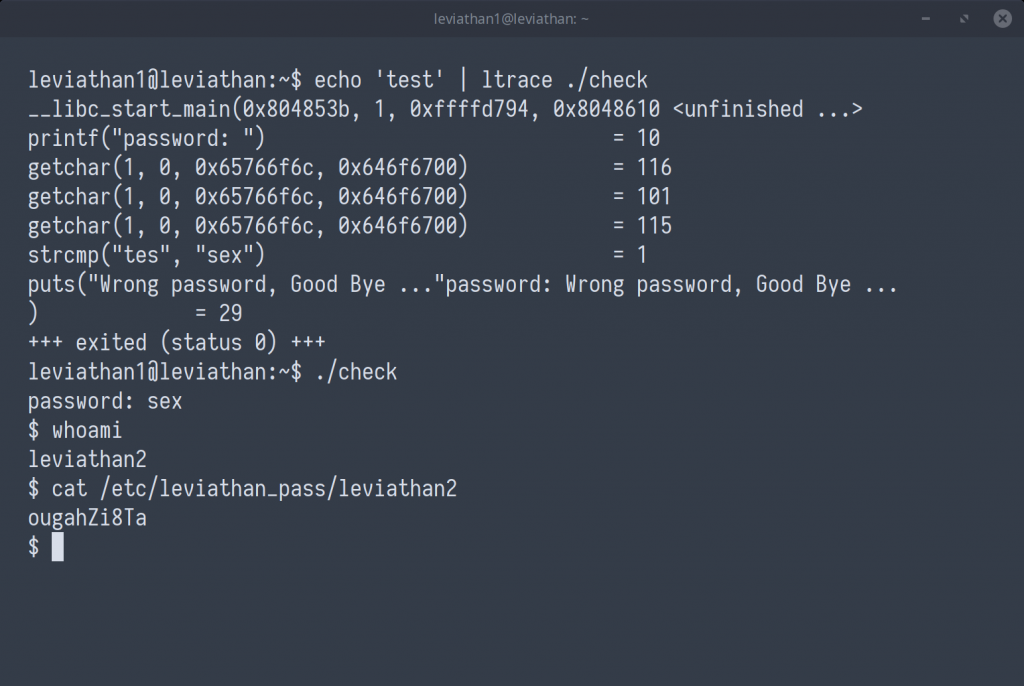
leviathan2 : ougahZi8Ta