OverTheWire Leviathan – Level 6

Executable leviathan6 prompts the user for a 4-digit password. Reviewing the executable with ltrace, strace, and strings produces nothing obvious, so let’s move on to the next most obvious step — brute-forcing.
There’re plenty of different ways to write up a script to brute-force leviathan6‘s 4-digit password. For this instance, I’m just going to use a for-loop.
for i in {0000..9999}; do echo -n "${i} - "; ./leviathan6 "${i}"; done
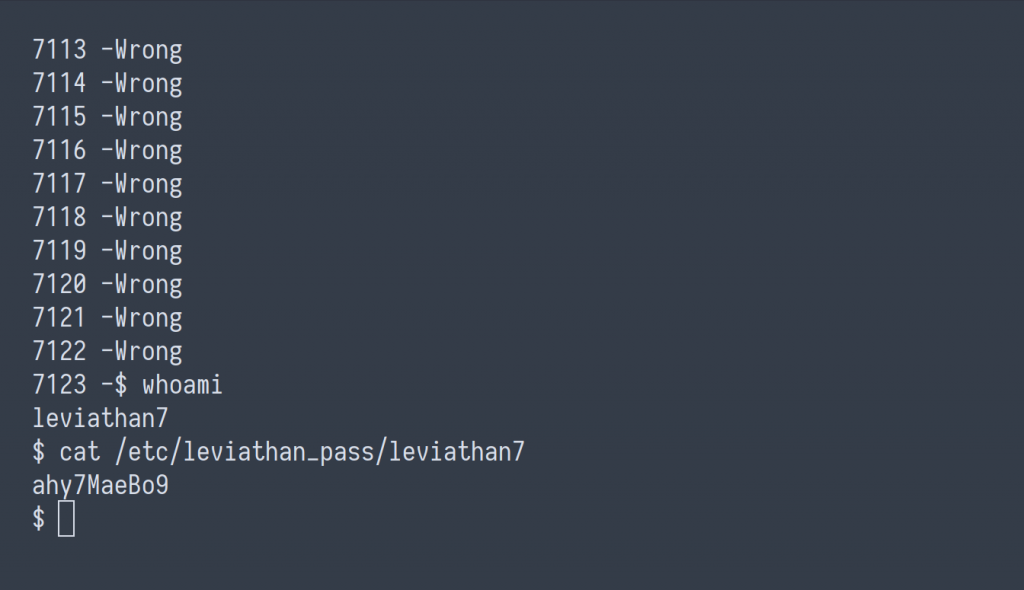
leviathan7 : ahy7MaeBo9